A question I’m asked quite often is, “Is WordPress secure?”
The answer is not at all obvious, and it’s more complex than you think…
But let’s start from the beginning… Is a new WordPress installation secure? that means is an “out-of-the-box” installation secure (without configuring anything but the basic settings)?
The answer is no….
Here are 12 good reasons why it is not!
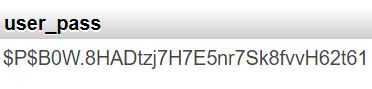
1) Admin user ID = 1
In a default installation, WordPress automatically assigns to the admin user the ID #1.
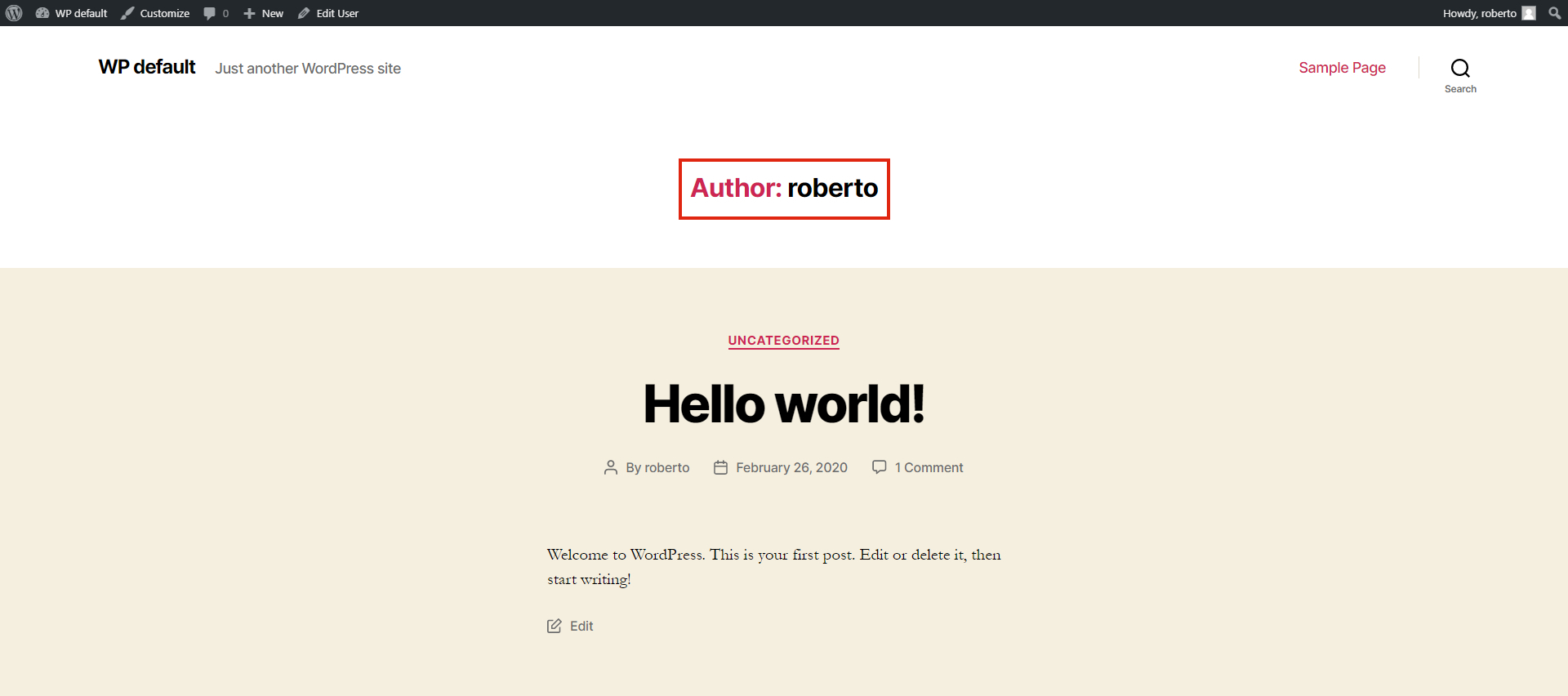
To find the login name of the administrator user, you just have to open your browser and type in the address field site_name/?author=1
At the top of the page (marked here with a red rectangle) you should see the administrator user login’s name!
Risk
Having the login name of the administrator user, means you already have the first part of user’s credentials… now you just have to find out his password!
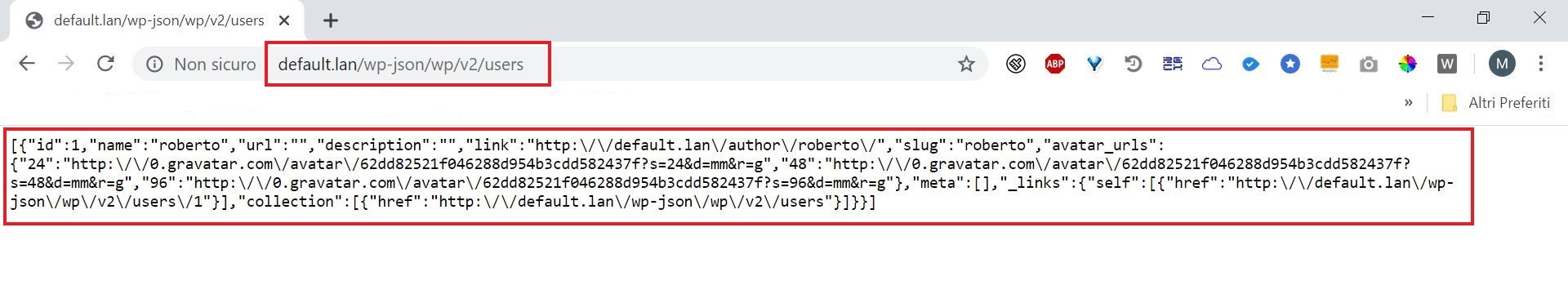
2) Rest API interface
The Rest API interface is a WordPress application programming interface, which allows to interact programmatically with a WordPress site.
The interface has several “endpoints” that offer access channels to the data on the WordPress site. One of these “endpoints” (“users”) allows to display the login names of all registered users on a WordPress site (both administrators and non-admin users).
Risk
Come nel punto precedente, avere a disposizione il nome di login dell’utente amministratore facilita l’individuazione della combinazione delle credenziali d’accesso utente/password.
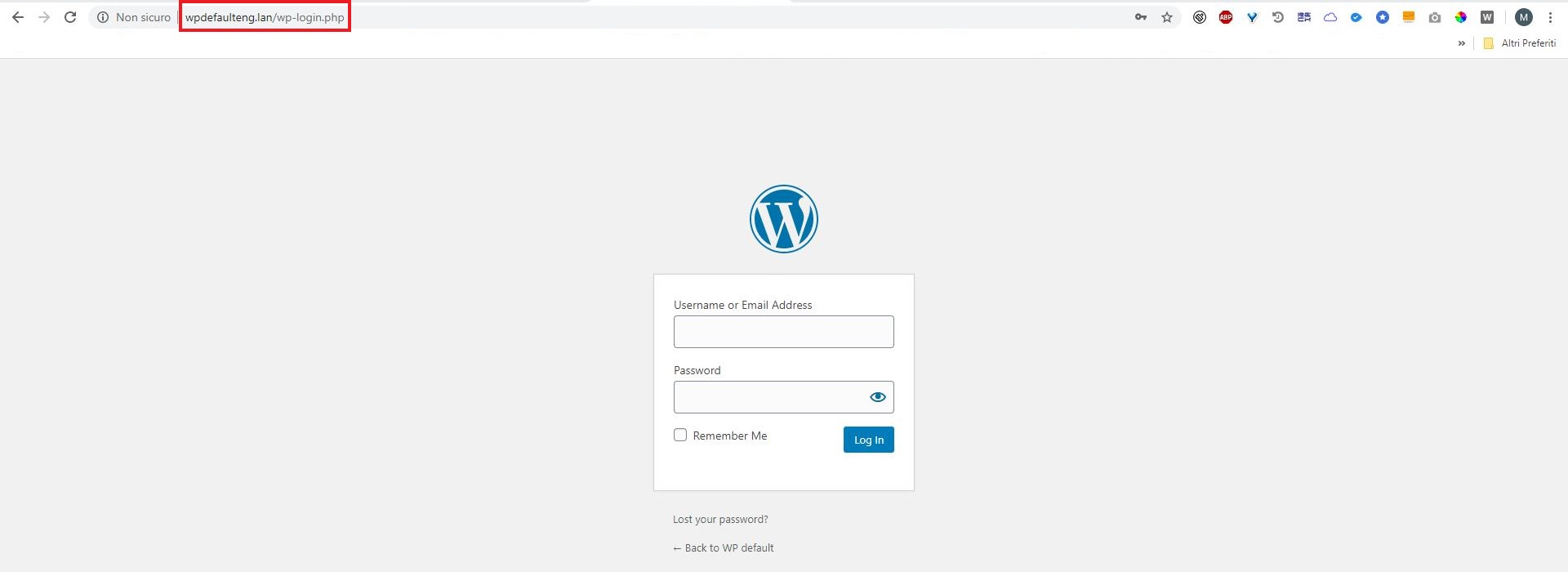
3) Default login page url
In a default installation, the login page url is site_name/wp-login.php
Risk
As we have seen above, to find the admin user login’s name is quite simple. If, in addition, the login page’s url is left unchanged, you just have to launch an automated script that will test a huge amount of passwords until you find it! (so-called “brute force” attack)
To give you an idea of how quickly a simple password can be found, you can watch this video:
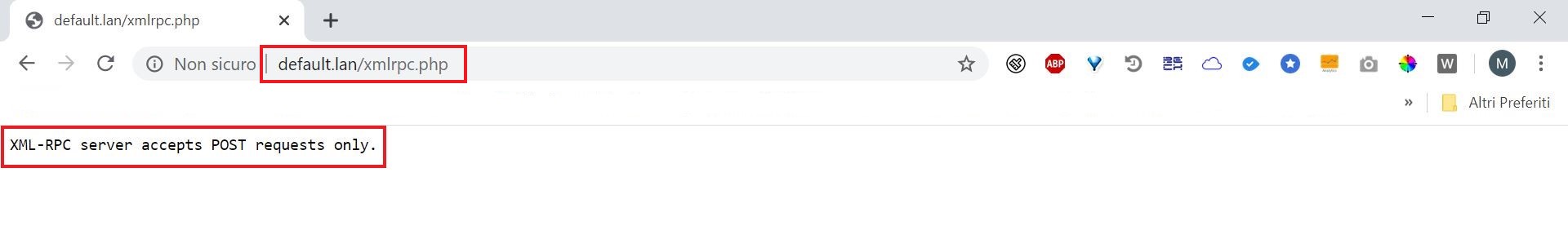
4) XML RPC interface
The XML RPC interface offers similar features to the Rest API interface, and also allows remote programmatic interaction with a WordPress site.
Risk
An enabled XML RPC interface allows to perform password guessing attacks through automated scripts.
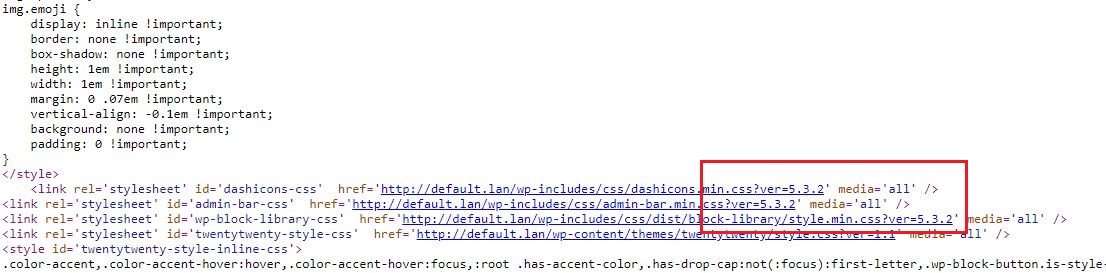
5) WordPress version number
In a default installation, the WordPress version number can be easily found by looking at the homepage’s source code in the stylesheets section:
Risk
Having the number of the installed WordPress version, you can immediately check on dedicated websites, which vulnerabilities have been found in the installed version, and use them to try to hack the website, especially if the installed version has not been updated to the latest version available.
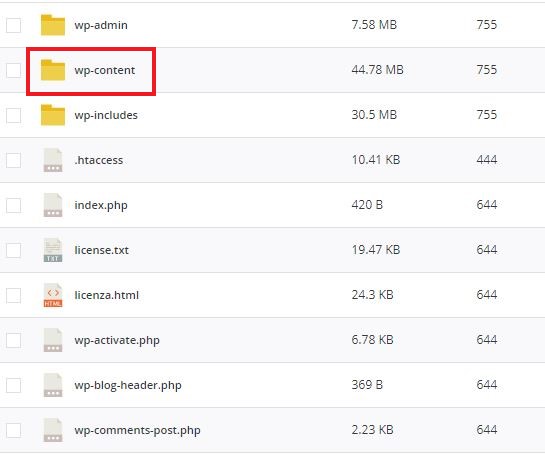
6) Default wp-content folder name
The default name of the folder where WordPress plugins and themes are installed is “wp-content”.
Risk
Malicious users use automatic scripts, called “bots” or “botnets” (in case of a network of “bots”), which scan the Internet for WordPress sites with vulnerable plugins or themes to exploit.
Leaving the default name of the wp-content folder unchanged, makes the work of bots much easier, as automated searches for plugins and themes are performed using the default name of the folder.
7) Password policy
WordPress features available for password management are just a few. Apart from checking password’s strength when creating a new user or during password updates, there are no other features available to increase system’s security.
Risk
In addition to use strong passwords (minimum 12 characters and a combination of uppercase, lowercase, numbers and symbols), a good password policy should also include 2-factor authentication and changing password regularly (time-limited passwords), all features that WordPress does not have natively.
For further information: “How to create hack-proof passwords“.
8) Password hashing
The hashing algorithm used by WordPress (MD5) to encrypt passwords is no longer considered secure since vulnerabilities were already found in 2004.
Risk
Getting a copy of a WordPress site’s database, and therefore the passwords hashes, has become much easier thanks to the use of simple tools such as search engines.
For further information: “How secure is the WordPress password’s algorithm?“.
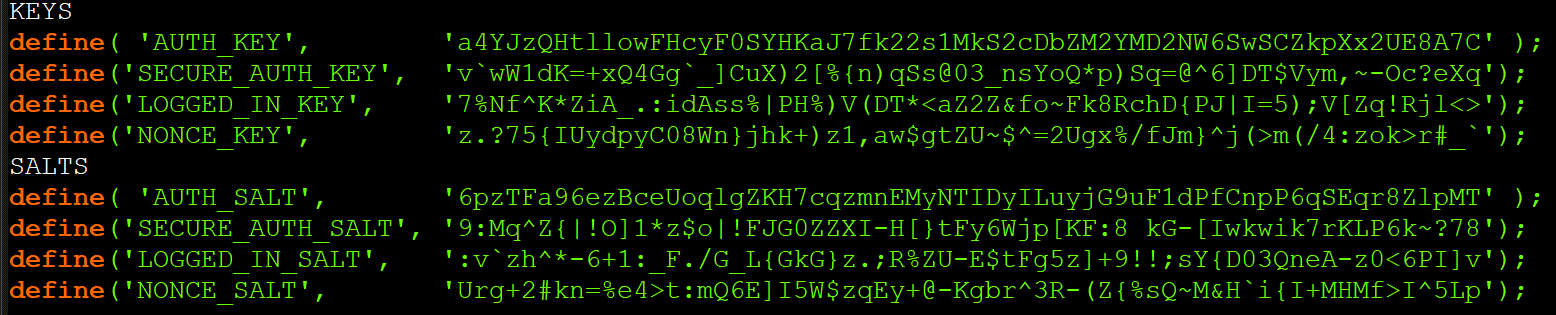
9) Updating Salts & Keys
Salts & keys are random character sequences saved in the wp-config.php file and used by WordPress to set passwords and cookies used by the system.
In a default installation, salts & keys are created during setup and after that they are no longer updated.
Risk
Having the salts & keys of your configuration file, a malicious user could create a cookie that would allow him to access your site with administrator privileges.
For further information: “WordPress salts, keys and cookies“.
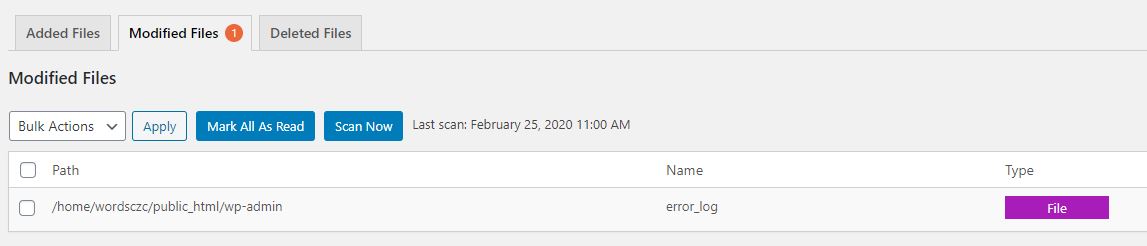
10) File changes detection
WordPress does not have natively a file changing detection system.
Risk
From a security point of view, it is very important to have a real-time detection system for any unwanted changes to the site’s files, including also a notification system via email or other means (text messages).
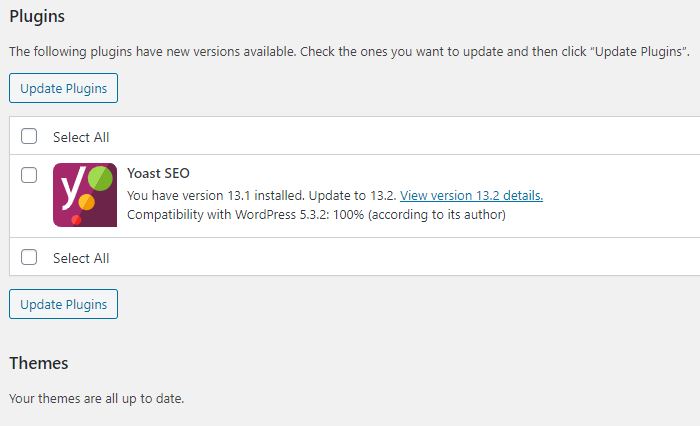
11) Theme and plugin updates
WordPress reports theme and plugin updates in the administration dashboard, both in the “Updates” section and in the “Plugins” and “Themes” sections. The problem, however, is that these reports are available only if you login into the administration dashboard, there is no notification system via email or other means (text messages). In addition, WordPress does not have a theme or plugin vulnerability reporting system.
Risk
Updating themes and plugins is a key operation to protect your WordPress site from malicious users. According to statistics released by the reference site WPScan Vulnerability Database (wpvulndb.com) the main vector of WordPress hacking are plugins’ vulnerabilities.
12) Web Application Firewall (WAF)
WordPress does not have a web application firewall natively. Such a firewall allows to block number of hacking threats, from “SQL injection” to dangerous “cross-scripting” attacks.
Risk
Cross-scripting and SQL injection attacks are among the most dangerous attacks for a WordPress site. The only way to protect your site is to implement a Web application firewall whose rules must be updated regularly in order to deal with new threats.
Conclusions
As explained above, the security of a freshly installed WordPress site is quite low (about 75%).
In order to achieve high levels of security, it is necessary to harden the system (both site and hosting server) and especially to implement a 24/7 security monitoring service, following the criticality of the website. The more critical the site, the higher the security.
Summary
| Security | Risk | |
|---|---|---|
| Freshly installed WP site | 75% | 50% |
| Hardened WP site | 85% | 25% |
| Monitored WP site | 95% | 10% |